It provides the ability to set up a phishing-style portal served by an Access Point (AP), where users are redirected before gaining internet access.
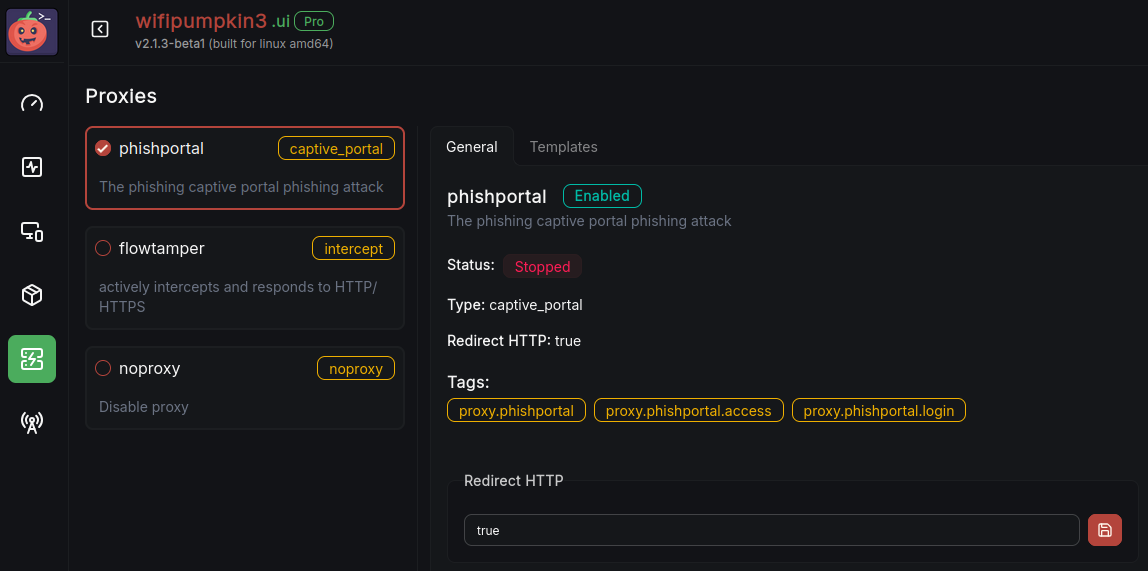
Phishportal
Phishportal Web UI Interface
- Build custom captive portal templates with HTML, CSS, and JavaScript.
- Define multi-step flows, allowing users to go through several pages (e.g., login, verification, confirmation) before internet access is granted.
- Validate form fields (such as username, password, email, or tokens) using customizable rules.
- Collect and log submitted data for analysis or security testing.
- Integrate with other modules such as proxies, DNS controllers, and firewall managers.
Key Features
- Template-based design – Each portal is built from customizable template folders.
- Step-based user flow – Users can be guided through multiple steps before network access.
- Flexible validation – Define validation logic for forms and fields.
- Integration-ready – Works seamlessly with the WiFiPumpkin3 Pro ecosystem.
Use Case
The Phishportal Proxy is typically used in red team operations, penetration testing, or network security research to simulate real-world captive portals.By mimicking legitimate login or verification processes, it helps assess the effectiveness of security awareness and incident detection mechanisms.
Next, you may want to check the How Phishportal Template Works guide to learn how to configure and deploy your first Phishportal template.